A to z reader login
Raz-Kids
- Books Read:
- Readers Online:
Kids Login
The award-winning website where K-5 students go to read — anytime, anywhere!
Get Free SamplesStart My Free TrialOrder Now
New to Raz-Kids? Watch our quick video introduction!
Raz-Kids delivers hundreds of interactive, leveled eBooks spanning 29 levels
- 400+ eBooks and open-book eQuizzes, with new books added every month, even in Spanish!
- Corresponding eQuizzes test comprehension, providing teachers with skill reports for data-driven instruction
- Online running records let teachers digitally assess each student, saving valuable classroom time
- The motivational "Raz Rocket" gets students excited about reading and strengthens the school-to-home connection
- A winner of numerous awards, including CODiE and EDDIE Awards and a Teachers' Choice Award for the Classroom
Free SamplesFree TrialOrder Now
Connecting Raz-Kids to Common Core ELA standards
400+ eBooks that students can listen to, read, and even record themselves reading
- Students can listen to books for modeled fluency, read books for practice, and then record themselves reading so teachers can monitor progress
- Every leveled eBook has an accompanying eQuiz to test reading comprehension
- Books include Spanish, Song, Nursery Rhymes, Poetry and more
- Because all books are available 24/7 via the Web, students can practice reading anytime, anywhere
Free SamplesFree TrialOrder Now
Check out powerful reporting on Raz-Kids
Raz-Kids makes reading accessible (and fun) like never before
- Access for Students: With Raz-Kids, students can practice reading anytime, anywhere - at home, on the go, and even during the summer!
- Keeping Teachers in Control: Teachers can make assignments and track student progress with online assessments and student recordings
- Results: Viewing reports is simple, for individuals, classrooms, schools and even districts!
- Common Core: See how Raz-Kids can support your efforts to succeed with Common Core ELA standards
Free SamplesFree TrialOrder Now
Students can read on-the-go from their favorite mobile device
Raz-Kids is now on the iPhone, and iPod Touch!
Besides the iPad, Android, and Kindle Fire tablets, students can now access their assignments right from their iPhones or iPod Touches! Read More
- On top of being accessible 24/7 via the Web, Raz-Kids also delivers reading access through its free apps, meaning your students can read and take quizzes on their iPad, Android, and Kindle Fire tablets.
- All student activity in the app is captured and reported to teachers at Raz-Kids.com, thus helping teachers monitor student progress and determine the instruction needed for each student.
Free SamplesFree TrialOrder Now
"I like how Raz-Kids motivates students to read. Students want to use the program, and it provides parents an alternative to getting students to read at home. I have seen students improve their reading level simply because they are practicing more."
Heidi Springer, Second Grade Teacher
Henry Hudson School #28; Rochester City School District; Rochester, New YorkMore Testimonials
2014 Teachers' Choice 2013 SIIA CODiE Award Winner 2013 Best Reading Resource Website, Teacher's Tools 2013 District Administration Top 100
Science A-Z
Kids Login
Science A-Z ensures that teachers have the resources they need to develop students' science knowledge and practices while also supporting key literacy skills.
- Thousands of resources to teach core science ideas and practices
- Multilevel books to differentiate reading instruction
- Hands-on experiments and projects to apply science concepts
Get More InfoStart Free TrialOrder Now
Differentiated Science Lessons and Activities for K-6 Students
Science A-Z is an award-winning curriculum resource that provides a robust library of multilevel informational texts, hands-on experiments, and other engaging learning opportunities.
- Differentiate instruction with multilevel reading materials offered across three grade spans (K-2, 3-4, and 5-6).
- Put science into practice with high-interest science activities and projects that foster curiosity and investigation.
- Expand students' understanding with additional current events and STEM-focused resources.

Learn More
Free Samples Free Trial Order Now
Customizable Lessons and Informational Texts
in Four Scientific Domains
Science A-Z offers an abundance of resources for teachers and students offered in comprehensive units across four scientific domains: Life, Earth and Space, Physical, and Process Science.
- Life Science Resources teach students about the living world around them and how organisms interact with one another.
- Earth and Space Science Resources teach students about features, materials, and processes on Earth and in outer space.
- Physical Science Resources teach students about the nature and properties of energy, forces, and matter.
- Process Science Resources teach students about the skills and tools necessary to conduct investigations and find answers.
Learn More
Free Samples Free Trial Order Now
Multilevel Texts that Seamlessly Integrate Science and Reading
Science A-Z provides a library of developmentally appropriate content to teach students science concepts, literacy skills, and the practices of science and engineering through printable and digital books and other resources.
- Satisfy both science and ELA curriculum standards with engaging content offered across three grade spans.
- Supplement instruction with hundreds of supporting texts, activity sheets, and lesson extensions that expand student understanding.
- Improve the home-to-school connection with engaging multilevel eBooks students can access anytime, anywhere.
Learn More
Free Samples Free Trial Order Now
Hands-On Learning Experiences for K-6 Students
Science is best learned through hands-on experiences.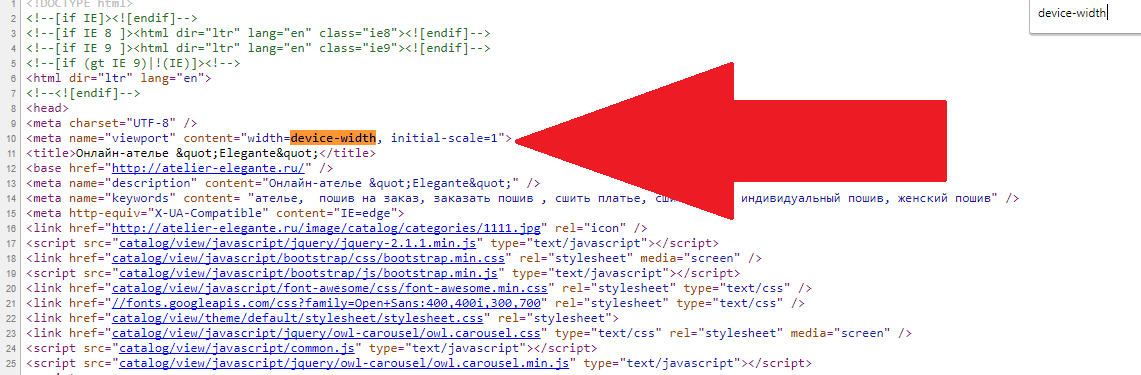 Science A-Z delivers an extensive collection of engaging activities, guided experiments, and open-ended projects that allow students to think and investigate like scientists and engineers.
Science A-Z delivers an extensive collection of engaging activities, guided experiments, and open-ended projects that allow students to think and investigate like scientists and engineers.
- Put science into practice with engaging experiments and activities that use everyday items to expand on unit concepts
- Promote collaboration and inquiry-based learning with open-ended challenges that require students to apply STEM practices.
- Encourage creativity and innovation with the resources necessary to conduct a science fair.
Learn More
Free Samples Free Trial Order Now
Login and password (username) - what is it, how to create and securely store them
Updated January 16, 2023 Views: 82 286 Author: Dmitry Petrov Hello, dear readers of the KtoNaNovenkogo. ru blog. It seems to be a simple question, but it still often arises among novice Internet users, when they create an account for the first time, they are asked to come up with a nickname, login and password.
ru blog. It seems to be a simple question, but it still often arises among novice Internet users, when they create an account for the first time, they are asked to come up with a nickname, login and password.
It would be better if I immediately warn and try to explain the importance of my logins and passwords that you have invented, because on the Internet they break everything, and not just where something is.
What is the login
So, the login is your individual identifier (must be unique for the service where you register). Now, on many services, it is allowed to use names or nicknames written in Russian letters as their logins, but earlier it was completely required to use only Latin characters and numbers when writing it.
This is apparently due to the fact that the data obtained during user registration (login and password) are stored in the database. Therefore, when entering my login, I use the same rule that it is permissible to use in URL addresses - [0-9],[a-z],[A-Z],[_],[-]. This spelling is suitable when registering for any service.
Therefore, when entering my login, I use the same rule that it is permissible to use in URL addresses - [0-9],[a-z],[A-Z],[_],[-]. This spelling is suitable when registering for any service.
What is a username
You should also understand how the login differs from the username . This confusion has its legs growing from the same rule mentioned above of using only Latin characters when registering, while on the forum, website, blog and social network where you register, it would be appropriate to use usernames (real or nicknames) written in Russian language.
Therefore, you often have to fill in two fields in the registration form: login (in Latin only) and name (in Russian). True, now on the Internet there is a general trend towards simplification, and there are fewer and fewer such sites where you are confused with incomprehensible fields with two similar concepts.
Now often use as their login just your mailbox address or the mobile phone number specified during registration. Moreover, you can use any of these identifiers (login, phone or E-mail). It is clear that I am not talking about forums, but about sites like Paypal or Ebey.
It’s also worth thinking about your login wisely, because your personal data (full name) indicated in it can help attackers apply social engineering methods to you if you inadvertently become an object of interest of such individuals (thus very often steal wallets in electronic payment systems , mail and social accounts, as well as much more).
In our digital age, you need to learn to be vigilant and overcome your innate gullibility. Don't think that no one needs you. They are needed, but not you specifically, but coupled with thousands more careless users like you. Accounts are taken away on stream, and then they are sold in bulk to spammers and other bad personalities.
In addition, please note that on most services, the login you created cannot be changed later , except perhaps by registering a new account. Therefore, try to think over in advance all the awkward moments that may arise about this.
A complex password is what will allow you to sleep peacefully. I'm talking about
password (password) . What it is? Ideally, this is a very difficult to select and difficult to predict set of characters that are not always letters or numbers. The more complex my password is, the more difficult it will be for attackers to hack my mailbox, account on a forum, website or social network with a simple enumeration of dictionaries. An example of bad options is your name typed in the Latin layout, options qwerty, 123456 and thousands of others, the lists of which are available to any cracker.
It is clear that you are insuring yourself in case you forget your password or lose the piece of paper on which it was written down. But anything that helps you recover it will help the cracker figure it out. The good old adage still applies: if you put it farther, you will take it closer.
Personally, I realized the need to use a reliable manager to store my passwords and logins only after stealing funds from my WebMoney wallet and after infecting almost all of my sites with viruses. In both cases, there was a banal theft of passwords (in the first case, it seems that my mailbox with a password equal to qwertyqwerty was hacked by brute force, and in the second, they pulled out my passwords for accessing sites via FTP, which were stored in plaintext in filezil).
Carelessness is always punishable, especially on the Internet, where the situation is similar to the dashing nineties in Russia. When choosing a password manager, I was guided by reviews on the Internet, and also by the fact that it was free and open source (any understanding programmer will be able to identify developer loopholes, if they exist).
When choosing a password manager, I was guided by reviews on the Internet, and also by the fact that it was free and open source (any understanding programmer will be able to identify developer loopholes, if they exist).
The latter is important, because trusting all your data to one single program is quite fraught. But if there are no “bookmarks” in the code, then it will be almost impossible to open the database without entering the master password or specifying the key file, because cracking the complex encryption key of the database with passwords by brute force can even take years on a supercomputer.
My password manager is KeePass . It can not only securely store the data loaded into it (login and password for each of your accounts anywhere), but also allows you to use them safely.
There are hotkeys for automatically filling in all fields in the authorization form on the site or in any program on your computer. There is also a powerful password generator with varying degrees of complexity. This program has the ability to share its encrypted database with various mobile applications, which makes it even more convenient and in demand.
There is also a powerful password generator with varying degrees of complexity. This program has the ability to share its encrypted database with various mobile applications, which makes it even more convenient and in demand.
Read about all the vicissitudes of working with KeePass in the article below and be sure to transfer all your logins and passwords from a piece of paper or a file in your computer to the encrypted Kipas database, which you store in the cloud just in case.
If you still prefer to use a text file on your computer for the created login and password, then at least store it in the folder with your password created by TrueCrypt.
The program is again free and open source - time-tested reliability. In general, be vigilant and do not even trust yourself in matters of security.
Good luck! See you soon on the pages of the blog KtoNaNovenkogo. ru
ru
How does the login-password work and at what point can hackers steal this data? - Social networks on vc.ru
The idea to use a password to enter accounts first came from the employees of the Massachusetts Institute of Technology. After some time, experts learned to use hashing to store passwords - an algorithm that stores a login-password pair in encrypted form.
5184 views
Hashing
When entering a password and login, the hash is checked first login. If the entered login exists, then the system takes the password, possibly already hashed, and compares it with the one in the internal user database. Further, many sites use to transfer traffic and information not a pair of login-password, but their hashes.
Surprisingly, but true - when hacking into user databases, hackers receive not lists of passwords, but a list of hashes. However, it will take years to decipher them due to the computations used for hashing that are difficult to reverse.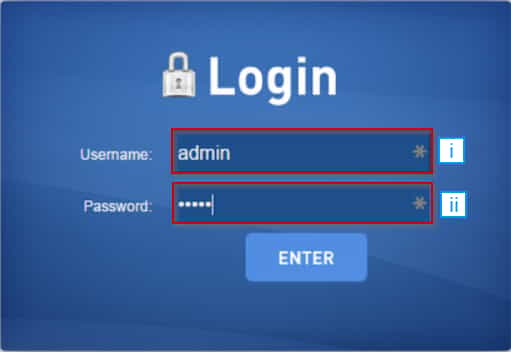 This method of stealing login and password is inefficient, even if there is a hashing algorithm.
This method of stealing login and password is inefficient, even if there is a hashing algorithm.
Guessing passwords
Therefore, hackers prefer another method of hacking - through guessing passwords. According to one study, 90% of online accounts use one of 10 thousand passwords. At the same time, many users, having forgotten the password, do not try to remember it, but immediately proceed to the password recovery procedure.
If you use an account in social networks or services for authorization on third-party sites, then a different method is used to enter the system: the site where you log in searches for any information by “cookies”, most often – “login-password”.
Therefore, pay attention to which sites store cookies: this is too important information to give it to outsiders.
Check your browser settings
Passwords also have another vulnerability - when a site associated with other web services or applications is hacked, attackers gain access to information on third-party sites. But this method of stealing logins and passwords - through hacking into more vulnerable resources - is used a little more often.
But this method of stealing logins and passwords - through hacking into more vulnerable resources - is used a little more often.
Obtaining a password using phishing
Why waste your energy to get a login-password if users will do it for you through their own inattention? Most often, the theft of the login and password is carried out using phishing sites. These web pages masquerade as known resources, tricking users into entering their real login passwords. After that, the site created to steal passwords transfers the information received to its developers and it is already used at the discretion of the attackers.
For example, several years ago there were several resources that pretended to be the site of the social network “Vkontakte”. Sometimes these resources promised advanced features: guest viewing, advanced settings and features. But they all pursued the same goal - stealing the password from VKontakte.
Pay attention to the accuracy of the site name and the security of the connection
Theft of passwords via e-mail
While fake password stealing sites are the most common form of phishing, there are other threats to user security.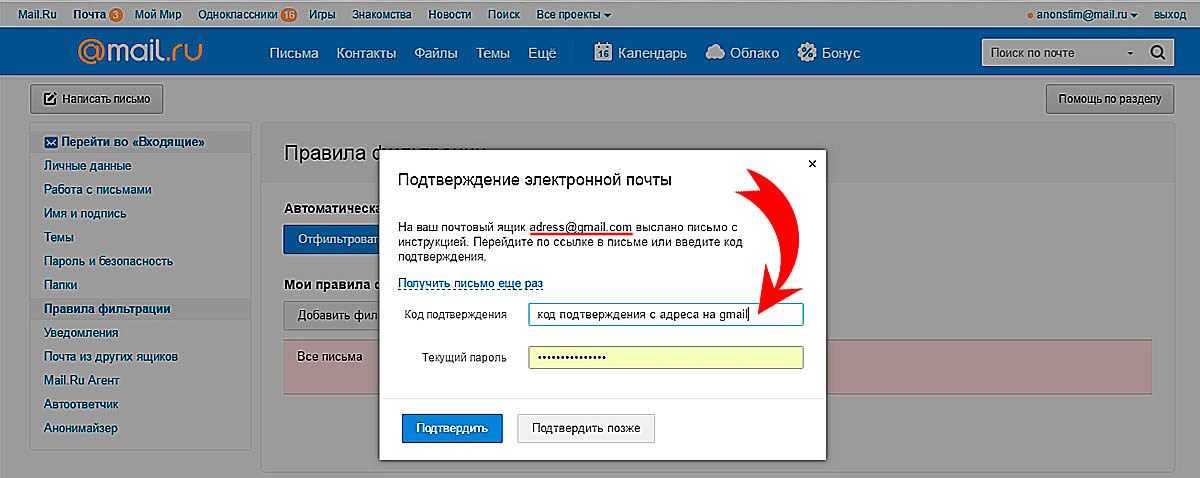 One popular method is to send out emails purporting to be a bank or a well-known company. You have most likely seen these letters, or their "relatives", where the subject of the letter begins with a first name address on behalf of a representative of a large company.
One popular method is to send out emails purporting to be a bank or a well-known company. You have most likely seen these letters, or their "relatives", where the subject of the letter begins with a first name address on behalf of a representative of a large company.
Previously, such letters infected computers and steal logins and passwords immediately after opening. Today, with the development of user cyber protection not only by anti-virus companies, but also by IT corporations-service providers, this mechanism no longer works. Therefore, cyber scammers come up with other ways of deception.
For example, they include links in emails to steal a password. This link is accompanied by text stating that privacy is at stake or that the user has won a big prize. By clicking on the “link” or downloading the file, the user is already endangering his personal data – phishing can start at any moment.
Password theft using keyloggers
In addition, some links contain programs for stealing passwords - keyloggers.