2 step instruction
30 Fun 2 Step Directions for Preschoolers
- Share
“Put your slippers on and grab a spoon for your cereal.” Easy to do, right?
For adults and older kids, following directions that have two steps can be quite an effortless task. For toddlers and young preschoolers, following multiple directions is a skill that takes time and maturity.
You can practise this skill in a fun way by using these 2 step directions for preschoolers.
What are Two Step Instructions?
Following directions that include two tasks is an important listening skill for children to learn. This helps them play games, follow instructions and procedures in the classroom and fit in socially with friends.
Being able to follow two-step instructions involves developing different types of skills.
Working memory is about holding onto information in order to use it. We want to be sure that kids can follow one-step directions effectively before moving ahead to giving them two steps to follow.
Auditory processing skills are also very important for enabling kids to follow directions they hear.
For example, auditory memory refers to when kids remember what they have heard, to use that information later.
Auditory closure helps them “fill in the blanks” when they have missed hearing the complete direction and auditory figure-ground aids kids in tuning out background noise to hear instructions. [source]
Speech therapy addresses not only how well children speak in words (expressive language) but also how well they understand what they hear (receptive language).
The receptive aspects of speech therapy are connected to auditory processing, and getting lots of practice in following directions is helpful to build those skills.
Verbal reasoning and vocabulary skills are also essential for children to comprehend your instructions. They must understand the words you are saying to be successful.
They must understand the words you are saying to be successful.
When Should a Child Follow 2 Step Directions?
At what age should a child start listening to and following one-to-two step directions?
At 24 months of age, many children can follow two or even three-step directions, especially those that are related, such as picking up two specific toys to put away on a shelf.
Although they can do this, research shows they choose to follow through only about half the time.
At around age three, most kids effectively follow two-step directions.
So then, when should a child follow 3 step directions?
Four-year-old children are usually able to follow through on three-step instructions, especially those that are given in a logical order.
[source]
How do I Teach My Child to Follow Multi-Step Directions?
It’s important to talk to your children often, giving voice to your own thought process as you move through your day. Verbalize what you observe about your child’s movements throughout the day, as well.
Verbalize what you observe about your child’s movements throughout the day, as well.
Read to your children, pointing to illustrations, and urging them to name objects.
How do you teach following instructions?
Listening skills in early childhood are very important and must be practised. Here are some tips:
- When giving your child instructions, state them clearly, in simple language, and give your child enough time to respond.
- Look at them when giving directions, and make sure they are looking at you.
- Restate or clarify if your child has not followed through on the instructions given.
- Model the correct actions, if necessary.
- Praise your child when they follow through on a single instruction and they will eventually build the ability to follow multiple part instructions.
- Don’t start giving 3 step directions until your child has mastered 2 instructions.
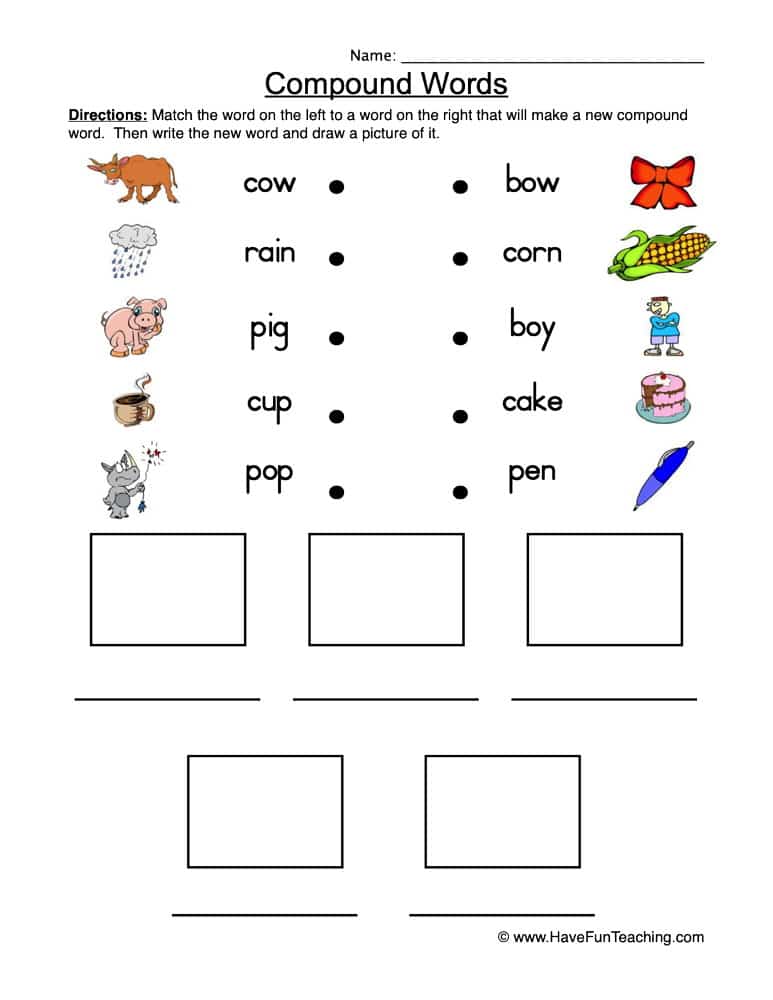
A list of 2 Step Directions for Preschoolers
Some of the following examples include 2 step directions with prepositions or spatial concepts, such as “on,” “under”, and “over. ”
”
These types of words address the relationships between objects or between objects and individuals and can help teach positional language.
Make a game out of requesting that your children complete two actions. You can also make it fun by using these directions in familiar games that require giving directions, such as “Simon Says” or “Follow the Leader.”
You could also play “Broken Telephone,” to see if the last person who hears the directions can follow through successfully.
Another fun game is Listen and Draw. Give multiple directions that your child must follow to draw the picture you describe.
[source]
Here is a list of instructions suitable for preschoolers:
1. Sit down on the floor and close your eyes.
2. Touch your head and turn in a circle.
3. Stand up and pretend to be frozen.
4. Bounce the ball and say your name.
5. Do a jumping jack and then sit on the chair.
6. Hop on one foot and smile.
7. Place the teddy bear under the table and sit on the chair.
8. Walk along the fence and sit on the swing.
9. Reach your hands over your head and clap your hands.
10. Stand next to Grandma/Grandpa and hold onto their hand.
11. Draw a yellow sun above the green grass.
12. Draw blue water next to a brown beach.
13. Touch your toes and then spin around in a circle.
14. Wash your face with this cloth and comb your hair.
15. Spread peanut butter on one slice of bread and place the other slice on top.
16. Pull your blanket up on the bed and arrange your stuffed animals.
17. Take a book out of your bag and set it on the table.
18. Lie down next to Mom/Dad and close your eyes.
19. Take off your mittens and hang them up to dry.
20. Point to your eyes and say your name.
21. Point to your lips and smack them together.
22. Turn off the TV and place the remote on the coffee table.
23. Stomp your feet and say, “I’m a dinosaur!”
24. Choose a book from your shelf and read it to your doll.
25. Cover your eyes and say, “Boo!”
26. Turn around in a circle and then sit down on the grass.
27. Wave goodbye to me and walk to the door.
28. Climb up the steps and then walk back down.
29. Fetch your school bag and put your lunch box inside it.
30. Wash your hands for dinner and come back to sit on a chair at the table.
These are just a jumping-off place to start your mind working! Involve your children and challenge them to make up their own directions and ask you to follow them!
Check out these other listening activities for kids to get even more practice!
Get FREE access to Printable Puzzles, Stories, Activity Packs and more!
Join Empowered Parents + and you’ll receive a downloadable set of printable puzzles, games and short stories, as well as the Learning Through Play Activity Pack which includes an entire year of activities for 3 to 6-year-olds.
Access is free forever.
Signing up for a free Grow account is fast and easy and will allow you to bookmark articles to read later, on this website as well as many websites worldwide that use Grow.
- Share
Unrelated 2 Step Directions - Speech Therapy Activities — Toddler Talk
Receptive Language Lessons
Written By Stephanie Keffer
Toddlers typically begin to follow directions with two unrelated steps just before their third birthday.
These directions include 2 different actions that are completely separate from one another. You can think of these directions as following this template: First do action 1 with item 1, Then go do action 2 with item 2. For example, “Push in your chair and go to the sink,” or “Take off your shoes and hang up your coat.”
For example, “Push in your chair and go to the sink,” or “Take off your shoes and hang up your coat.”
These types of directions are more complex and therefore more challenging than two-step directions with a single item.
As you practice, keep in mind that your toddler’s success in following directions will vary based on how tired they are, their general mood, and their current level of attention. Day-to-day fluctuations are expected and completely normal.
Speech therapy tips for practicing with 2 step unrelated directions
Tip 1 - Create two-step unrelated directions
In this lesson, we’ll focus on following directions that:
Have two or more steps (two different actions with two different items)
Have not been practiced before and are not part of a daily routine
Are __NOT__ related to an activity your child is doing when you give the direction.

For example, if your child is coloring on the floor, you could tell them, *“Sit at the table and open the Play-Doh.”* If they’re playing with a babydoll, you could say, “Oh no, your shark looks hungry and sleepy! *Feed the shark* and *put him to sleep*.”
Tip 2 - Offer the minimum amount of help your child needs
As you practice following directions with your child, it’s best to practice at a level where your child can successfully complete a direction with minimal help. Follow this step-by-step breakdown to help wean your child off of needing your assistance to complete directions. If your child completes the direction at any point, you do not need to continue with the remaining attempts. Praise your child for completing the two-step direction correctly. (“Yay, you got the cow and gave him a cookie!”).
Here are the steps:
Say your child is playing with a toy turtle. Start by giving the direction, “Get the cow and give him a cookie.
 ” Don’t offer any visual clues about what you want them to do, like motioning with your eyes or hands.
” Don’t offer any visual clues about what you want them to do, like motioning with your eyes or hands. If your child is unable to complete the direction on their own, repeat the direction and offer one piece of help, such as pointing to what you want your child to do. Say, “Get the cow and give him a cookie,” point to their cow, and then point to the cookie.
For your third attempt, repeat the direction again, but break it into two parts. First, say “Get the cow.” Once they grab the cow, then say “Give the cow a cookie.”
Finally, you can complete the direction together. Repeat the direction, and then actually help your child through the actions. Say “Get the cow and give him a cookie” as you guide your child to get the cow and feed it a cookie.
You’ll know your child has mastered this skill once they can consistently follow your directions in at least four out of five tries.
Tip 3 - Expand your child’s vocabulary to help them follow directions
Following directions is a perfect opportunity to teach your child the meaning of new words. If you discover during practice that your child does not understand the meaning of a particular word, incorporate that word into your daily activities. For example, if you discover that your child doesn’t know what “scrub” means, talk about SCRUBBING your hands in the sink while you wash, and have them help you SCRUB pots and pans after dinner. As always, practice learning just a few words at a time to prevent you AND your child from feeling overwhelmed.
If you discover during practice that your child does not understand the meaning of a particular word, incorporate that word into your daily activities. For example, if you discover that your child doesn’t know what “scrub” means, talk about SCRUBBING your hands in the sink while you wash, and have them help you SCRUB pots and pans after dinner. As always, practice learning just a few words at a time to prevent you AND your child from feeling overwhelmed.
And I will be the first to admit that thinking of these directions on the fly when you’re playing isn’t easy! We created 3 different activities with items and toys most people have. For each activity we’ve listed out directions you can practice with for this lesson!
Download our PDF activities guide for practicing with 2 step directions - speech therapy at home practice ↓
Practicing with 2 step directions - speech therapy at home activity
Washing Hands Before Snack
Materials: Set-up:Gather the items you need for your snack so that your child sees that it is almost snack time.
In this activity, you will be helping your child understand 2-step directions where the parts are unrelated. The second part of the direction is “wash your hands” and the first part is something else in your home.
You will practice this skill before snack time, if your child likes snacks. If they don’t, pick another daily activity that your child looks forward to. You will tell them something simple to do, and then to go wash their hands. You will say, “it is almost time for snack! But first, put your shoes in your room and wash your hands.” Or “throw the wrapper in the trash and then wash your hands”, “put the cars in the box and then wash your hands.” The first part of your direction should be something your child already does, but maybe they don’t always do it routinely before washing.
If they follow the direction correctly, celebrate that your child did it correctly by repeating what they did (“Yay, you put your shoes away and washed your hands!”) If your child does not do it, repeat the direction again.
If they do not follow the direction the second time, break up the direction into two parts. Say, “put your shoes away” and wait for your child to put their shoes away. Then say, “go wash your hands.” Then celebrate by repeating what they did (“Yay, you put your shoes away and washed your hands!”)
What to say:Here are examples of 2 step directions you may use:
“Throw the wrapper away and go wash your hands.”
“Put the book away and go wash your hands.”
“Give me my phone and go wash your hands.”
“Put the banana on the table and go wash your hands.”
Download our PDF activities guide for practicing with 2 step directions - speech therapy at home practice ↓
© 2020-2022. Stephanie Keffer, MS CCC-SLP. All Rights Reserved.
The content offered on ToddlerTalk.com is for informational purposes only. Toddler Talk is not engaged in rendering professional advice, whether medical or otherwise, to individual users or their children or families. No content on this site, regardless of date, should ever be used as a substitute for direct medical advice from your doctor, speech language pathologist, or other health professional. By accessing the content on ToddlerTalk.com, you acknowledge and agree that you are accepting the responsibility for your child’s health and well-being. In return for providing you with information related to home speech and language practice, you waive any claims that you or your child may have as a result of utilizing the content on ToddlerTalk.com
No content on this site, regardless of date, should ever be used as a substitute for direct medical advice from your doctor, speech language pathologist, or other health professional. By accessing the content on ToddlerTalk.com, you acknowledge and agree that you are accepting the responsibility for your child’s health and well-being. In return for providing you with information related to home speech and language practice, you waive any claims that you or your child may have as a result of utilizing the content on ToddlerTalk.com
Stephanie Keffer
What to choose for two-factor authentication instead of codes in SMS
Over the past couple of years, the idea of two-factor authentication, which the geeks have been talking about for so long, has greatly advanced to the masses. However, until now, in most cases, we are talking about two-factor authentication using one-time passwords sent via SMS. And this, unfortunately, is not a very reliable option. Here's what can go wrong:
Here's what can go wrong:
- You can spy on your SMS password if you have notifications on your lock screen turned on.
- Even if notifications are disabled, you can remove the SIM card from your smartphone, install it in another smartphone, and receive SMS with a password.
- SMS with a password can be intercepted by a Trojan that has made its way into the smartphone.
- Also, with the help of various frauds (persuasion, bribery, collusion, and so on), you can get a new SIM card with the victim's number in a mobile phone shop. Then SMS will be sent to this card, and the victim's phone will simply not connect to the network.
- Finally, SMS with a password can be intercepted through a fundamental vulnerability in the SS7 protocol over which these SMS are transmitted.
It should be noted that even the most time-consuming and high-tech of the listed methods of intercepting a password in SMS - by hacking the SS7 protocol - has already been used in practice. So it's not about the theoretical possibility of trouble, but about a very practical threat.
So it's not about the theoretical possibility of trouble, but about a very practical threat.
In general, SMS passwords are not very secure, and sometimes even very insecure. Therefore, it makes sense to attend to the search for alternative options for two-step authentication, which we will talk about today.
One-time codes in a file or on paper
The simplest replacement for one-time passwords sent via SMS is the same one-time passwords, but prepared in advance. This is not the worst option, especially for those services in which you need to log in relatively rarely. Actually, even for the same Facebook, this method may well be suitable, especially as a backup login method.
It works very simply: upon request, the service generates and displays a dozen one-time codes on the screen, which can later be used to confirm entry into it. Then you simply print or copy these codes on paper and put them in the safe. Or, even easier, save in encrypted records in a password manager.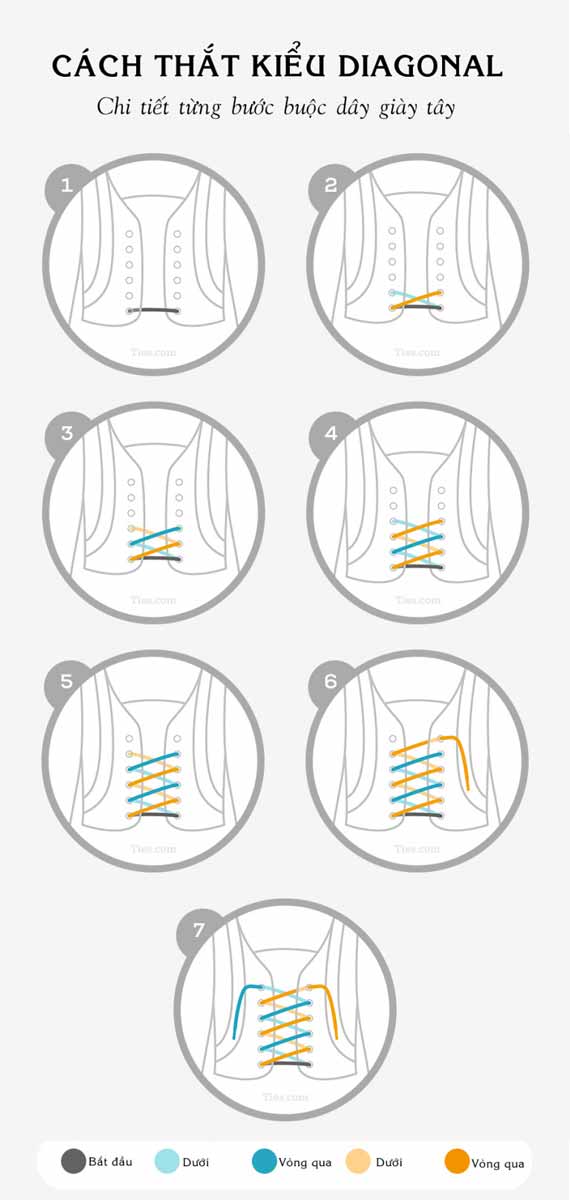
In general, it doesn't matter if you store these codes on warm lamp paper or in soulless digital form - it's important to store them so that they a) won't get lost and b) can't be stolen.
Applications for two-factor authentication
A set of one-time codes generated once has one drawback: sooner or later it will end, and it may well turn out that you will be left without a code at the most inopportune moment. Therefore, there is a better way: you can generate one-time codes on the fly using a small and usually very simple authenticator application.
How authenticator apps work
Two-factor authentication apps work very simply. Here's what you have to do:
- install an application for two-factor authentication on your smartphone;
- go to the security settings of the service, which offers the use of such applications among the options for two-factor authentication;
- choose two-factor authentication using the application;
- the service will show you a QR code that can be scanned directly in the 2FA application;
- you scan the code with the app and it starts creating a new one-time code every 30 seconds.
Codes are generated based on a key that is known only to you and the server, as well as the current time, rounded up to 30 seconds. Since both components are the same for you and the service, the codes are generated synchronously. This algorithm is called OATH TOTP (Time-based One-time Password), and in most cases it is used.
There is also an alternative - the OATH HOTP (HMAC-based One-time Password) algorithm. Instead of the current time, it uses a counter that increments by 1 each time a new code is generated. But this algorithm is rarely seen in reality, because when using it, it is much more difficult to ensure the synchronous creation of codes on the service and application side. Simply put, there is a considerable risk that at one not-so-great moment the counter will go wrong and your one-time password will not work.
So OATH TOTP can be considered a de facto industry standard (although formally it's not even the standard , which the creators of this algorithm strongly insist on in its description).
Compatibility of two-factor authentication applications and services
The vast majority of two-factor authentication applications work on the same algorithm, so for all services that support authenticators, you can use any of them - whichever you like.
As with any good rule, there are a certain number of exceptions to this one. Some services, for some reason only known to them, prefer to make their own two-factor authentication applications that work only with them. Moreover, the services themselves do not work with any other applications than their own.
This is especially common among large publishers of computer games - for example, there are Blizzard Authenticator applications that are incompatible with third-party services, Steam Mobile with a built-in Steam Guard authenticator, Wargaming Auth, and so on. For these services, these applications will have to be installed.
Adobe has also gone down this strange path by developing the Adobe Authenticator, which works only with AdobeID accounts. But at the same time, you can use AdobeID and other authenticators to protect, so it’s generally not clear why it was to fence the garden.
But at the same time, you can use AdobeID and other authenticators to protect, so it’s generally not clear why it was to fence the garden.
Anyway, most normal IT companies do not restrict users in choosing a 2FA application. And even if, for some reason, they want to control this process and create their own application, then most often they allow you to protect not only “their” accounts with it, but also accounts of third-party services.
So just choose the authenticator app that you like best for the set of additional features - it will work with most services that generally support 2FA applications.
Best Apps for Two-Factor Authentication
The choice of 2FA apps is surprisingly wide: searching for "authenticator" on Google Play or the Apple App Store returns dozens of results. We do not recommend installing the first application that comes across - this can be unsafe, because, in fact, you are going to trust it with the keys to your accounts (it will not know your passwords, of course, but you add 2FA precisely because passwords tend to leak) . In general, it is worth choosing from applications created by large and respected developers.
In general, it is worth choosing from applications created by large and respected developers.
Although the basic function of all these applications is the same - generating one-time codes using the same algorithm, some authenticators have additional functions or interface features that you may find convenient. We list some of the most interesting options.
1. Google Authenticator
Supported platforms: Android, iOS
Google Authenticator is the easiest two-factor authentication app to use. It doesn't even have settings. All you can do is add a new token (that's the name of the code generator for an individual account) or delete one of the existing ones. And to copy the code to the clipboard, just touch it with your finger on the touch screen of your smartphone or tablet. All!
However, this simplicity has a drawback: if you don't like something in the interface or want something more from the authenticator, you will have to install another application.
+ Very easy to use.
2. Duo Mobile
Supported platforms: Android, iOS
Duo Mobile is also extremely easy to use, minimalistic and lacks additional settings. Compared to Google Authenticator, it has one advantage: by default, Duo Mobile hides codes - to see the code, you need to click on a specific token. If you, like me, feel uncomfortable every time you open the authenticator and show everyone around you a bunch of codes from all your accounts at once, then you will definitely like this feature of Duo Mobile.
+ Hides codes by default.
3. Microsoft Authenticator
Supported platforms: Android, iOS
Microsoft also did not complicate and made its authenticator look very minimalistic. But at the same time, Microsoft Authenticator is noticeably more functional than Google Authenticator. Firstly, although by default all codes are shown, each of the tokens can be separately configured so that the code is hidden when the application starts.
Second, Microsoft Authenticator makes it easy to sign in to Microsoft accounts. In this case, after entering the password, it will be enough to press the login confirmation button in the application - and that’s it, you don’t even have to enter a one-time code.
+ Can be configured to hide codes.
+ Additional options for signing in to Microsoft accounts.
4. FreeOTP
Supported platforms: Android, iOS
There are four reasons why you might like this Red Hat authenticator. First, it's your choice if you love open source software. Secondly, this is the smallest application of all considered - the iOS version is only 750 KB. For comparison, the minimalistic Google Authenticator takes up almost 14 MB, and the Authy application, which we will discuss below, is as much as 44 MB.
Thirdly, by default, the application hides the codes and shows them only after touching. Finally, fourthly, FreeOTP allows you to configure tokens manually as flexible as possible, if you need it for some reason. Of course, the usual way to create a token by scanning a QR code is also supported.
Of course, the usual way to create a token by scanning a QR code is also supported.
+ Hides codes by default.
+ The application is only 700 Kb.
+ Open code.
+ Maximum settings when creating a token manually.
5. Authy
Platforms supported: Android, iOS, Windows, macOS, Chrome
. This allows you to access tokens from any of your devices. At the same time, this makes it easier to move to new devices - you do not have to re-activate 2FA in each service, you can continue to use existing tokens.
In the cloud, the tokens are encrypted with a key generated from a user-specified password, meaning that the data is stored securely and will not be easy to steal. You can also set a PIN code to enter the application - or protect it with a fingerprint if your smartphone is equipped with an appropriate scanner.
The main disadvantage of Authy is that the application requires you to create an account linked to your phone number right away - without this, you simply won't be able to start working with it.
+ Tokens are stored in the cloud, which allows you to use them on all your devices.
+ For the same reason, it is very convenient to move to a new device.
+ Entrance to the application is protected by a PIN code or a fingerprint.
+ Only the code for the last used token is shown on the screen.
+ Unlike other applications, it supports not only Android and iOS, but also Windows, macOS and Chrome.
- Requires you to register with Authy using your phone number - without this, the application does not work.
6. Yandex.Key
Supported platforms: Android, iOS
On the one hand, it does not require you to register right away - you can start using it with the same ease as Google Authenticator. On the other hand, it has several additional features that open up for those who are not too lazy to go into the settings.
First, "Yandex.Key" can be "locked" with a PIN code or a fingerprint. Secondly, you can create a password-protected backup copy of tokens in the Yandex cloud (but at this stage you will already have to provide a phone number) and restore it on any of the devices you use. Similarly, it will be possible to transfer tokens to a new device when you need to move.
Secondly, you can create a password-protected backup copy of tokens in the Yandex cloud (but at this stage you will already have to provide a phone number) and restore it on any of the devices you use. Similarly, it will be possible to transfer tokens to a new device when you need to move.
It turns out that "Yandex.Key" combines the simplicity of Google Authenticator and the advanced functionality of Authy - depending on what you prefer. The only drawback of the application is the interface that is not quite convenient for use with a large number of tokens.
+ Minimalism at the start, advanced functionality is available through the settings.
+ Create backups of tokens in the cloud for use on multiple devices and moving to new ones.
+ Entrance to the application is protected by a PIN code or a fingerprint.
+ Only the code for the last used token is shown on the screen.
+ Replaces the permanent password for the Yandex account.
- With a large number of tokens, it is not very convenient to search for the right one.
FIDO U2F Iron Authenticators: YubiKey and everything
key and put it in your pocket, then I have good news for you: this option also exists. These are hardware tokens of the U2F (Universal 2nd Factor) standard created by the FIDO Alliance.
How FIDO U2F tokens work
Hardware U2F tokens are very popular among security specialists, primarily because they work very simply from the user's point of view. To get started, just connect the U2F token to your device and register it in a compatible service, and this is done in just a couple of clicks.
Subsequently, if you need to confirm the entrance to this service, you will need to connect the U2F token to the device from which you are logging in and press the button on the token (in some devices, enter a PIN or put your finger on the scanner). That's all - no complicated settings, input of long sequences of random characters and other dances with a tambourine, which usually everyone imagines at the mention of the word "cryptography".
Insert the key and press the button - and that's really all
At the same time, "under the hood" everything is arranged very cleverly and cryptographically secure: when registering a token on the service, a pair of cryptographic keys is created - private and public. The public key is stored on the server, while the private key is stored in the Secure Element, which is the heart of the U2F token, and this key never leaves the device.
The private key is used to encrypt the login confirmation that is sent to the server and can be decrypted using the public key. If someone on your behalf tries to send a login confirmation encrypted with the wrong private key, then decryption using the public key known to the service will result in nonsense instead of confirmation, and the service will not let it into your account.
What are U2F devices
The best known and most common example of U2F is YubiKey, which is manufactured by Yubico. Actually, she stood at the origins of this standard, but chose to make it open, for which the FIDO Alliance was created. And since the standard is open, you are not limited in your choice: U2F-compatible devices are manufactured and sold by different companies - you can find many different models in online stores.
And since the standard is open, you are not limited in your choice: U2F-compatible devices are manufactured and sold by different companies - you can find many different models in online stores.
YubiKey - probably the most popular U2F tokens
For example, Google recently introduced its Google Titan Security Keys hardware authenticator suite. In fact, these are keys produced by Feitian Technologies (the second most popular manufacturer of U2F tokens after Yubico), for which Google has written its own firmware.
Of course, all hardware authenticators that are compatible with the U2F standard will work equally well with all services that are also compatible with this standard. However, there are several important differences between different models, and the most important of them are the interfaces that the “dongle” is equipped with. It directly depends on what devices it can work with:
USB - for connecting to computers ( Windows, Mac or Linux - it doesn't matter, the "keys" work without installing any drivers). In addition to the usual USB-A, there are "keys" with USB-C.
In addition to the usual USB-A, there are "keys" with USB-C.
NFC - required for use with smartphones and tablets on Android .
Bluetooth - needed on those mobile devices that do not have NFC. For example, iPhone owners still need a Bluetooth authenticator: despite the fact that iOS has already allowed applications to use NFC (until 2018, only Apple Pay allowed it), the developers of most U2F-compatible applications have not yet taken advantage of this opportunity. Bluetooth authenticators have a couple of disadvantages: firstly, they need to be charged, and secondly, they take much longer to connect.
The basic models of U2F tokens usually only support U2F itself - such a key will cost $10-20. There are more expensive devices ($20-50) that can also work as a smart card, generate one-time passwords (including OATH TOTP and HOTP), generate and store PGP encryption keys, and can be used to log into Windows, macOS and Linux and so on.
What to choose: SMS, application or YubiKey?
There is no universal answer to this question - for different services, you can use different options for two-factor authentication in various combinations. For example, the most important accounts (say, your main mail, to which the rest of the accounts are linked) should be protected to the maximum - locked to the “iron” U2F token and prohibited any other 2FA options. So you can be sure that no one will ever get access to the account without this token.
A good option is to link two "keys" to your account, as is done with car keys: one is always with you, and the other is in a safe place - in case the first one gets lost. At the same time, “keys” can be of different types: say, an authenticator application on a smartphone as the main one and a U2F token or a piece of one-time passwords lying in a safe as a backup.
Anyway, the main advice is to avoid using one-time passwords in SMS whenever possible. True, this will not always work out: for example, financial services, due to their conservatism, continue to use SMS and extremely rarely allow you to use anything else.
Coronavirus vaccination with Kovivac is contraindicated during pregnancy
February 20, 2021, 07:59,
/TASS/. Pregnancy and breastfeeding are contraindications for the use of the Kovivak coronavirus vaccine, follows from the instructions for the drug, posted on Saturday on the website of the state register of medicines.See also
Russian coronavirus vaccines. Characteristics and features of studies
"Contraindications: <...> pregnancy and breastfeeding," the document says.
It is noted that the efficacy and safety of the drug during this period have not been studied, so its use is contraindicated.
"Kovivak" is also contraindicated in case of serious reactions after administration of the drug (temperature above 40 degrees, hyperemia or edema more than 8 cm in diameter) or complications such as collapse or shock-like state that developed within 48 hours after vaccination. For convulsions that have occurred with any previous vaccination, this drug should also not be used.
Other contraindications for the use of Kovivac include severe allergic reactions. Children under 18 years of age are also prohibited from administering the drug.
"Temporary contraindications: <...> chronic infectious diseases in the acute stage. Vaccination is carried out during remission," the document says. It is noted that for such people the possibility of vaccination is determined by the attending physician.
Other contraindications
Other temporary contraindications for the use of the Kovivac vaccine include acute febrile conditions, acute infectious and non-infectious diseases. In this case, vaccination is carried out 2-4 weeks after recovery. With mild SARS and acute intestinal infections, vaccination can be carried out after the temperature normalizes and the acute symptoms of the disease disappear.
The drug should be used with caution in chronic diseases of the liver and kidneys, severe disorders of the neuroendocrine system, severe diseases of the hematopoietic system, diseases of the central nervous system, cardiovascular, bronchopulmonary, immune systems, gastrointestinal tract. "The attending physician must evaluate the benefit-risk ratio of vaccination in each case," the document says.
"The attending physician must evaluate the benefit-risk ratio of vaccination in each case," the document says.
Special instructions
The instructions for the drug also indicate that inactivated vaccines are not contraindicated in patients with an immunosuppressive or immunodeficient state, however, there are no clinical data on the use of the drug in this category of patients.
"Patients receiving immunosuppressive therapy and patients with immunodeficiency may not develop a sufficient immune response. Therefore, the use of drugs that suppress the function of the immune system is contraindicated for at least one month before and after vaccination due to the risk of reduced immunogenicity," states in the text.
Storage of the vaccine created by the MP Chumakov Center is allowed at a temperature of two to eight degrees Celsius for six months. The instructions note that the immune response after the introduction of "Kovivak", as well as after other vaccines, may not occur in everyone. "The vaccine stimulates the production of immunity against the coronavirus infection caused by the SARS-CoV-2 coronavirus. The protective antibody titer is currently unknown. The duration of immunity is unknown. Clinical studies to study projective efficacy have not been conducted," the document says.
"The vaccine stimulates the production of immunity against the coronavirus infection caused by the SARS-CoV-2 coronavirus. The protective antibody titer is currently unknown. The duration of immunity is unknown. Clinical studies to study projective efficacy have not been conducted," the document says.
Interval between doses
The interval between the first and second doses of the Kovivac vaccine is two weeks, according to the instructions for the drug.
"The vaccine is injected into the deltoid muscle (the upper third of the outer surface of the shoulder) twice with an interval of two weeks at a dose of 0.5 ml," the instructions say.
It is noted that there is no data on the interchangeability of Kovivak and other coronavirus vaccines to complete the course of vaccination. "Persons who received one dose of the Kovivac vaccine <...> must receive a second dose of the same vaccine to complete the vaccination course," the text of the instruction says. In addition, due to the lack of data on the compatibility of "Kovivak" with other drugs, the vaccine cannot be mixed with anything in the same syringe.
Adverse reactions
Adverse reactions from vaccination with Kovivac may occur within 1-3 days, the duration of reactions does not exceed three days.
"Adverse reactions may appear 1-3 days after injection. The duration of reactions usually does not exceed three days," follows from these instructions.
It is noted that during clinical trials of the drug, the most frequent reactions were local reactions (pain and induration at the injection site in 15% and 1% of the number of vaccinations, respectively) and general reactions (headache (up to 2% of those vaccinated) and short-term hyperthermia (up to 1%). "Mild reactions were more common. There were no severe local and systemic reactions to vaccination," the text notes.
In this case, the development of allergic reactions, syncopal conditions (reaction to the procedure for administering the drug) and an increase in lymph nodes is not ruled out. Infrequently, after vaccination, an increase in body temperature was observed. "It is not excluded the addition of acute (for example, acute respiratory viral infections, etc.) or exacerbation of chronic infectious diseases due to temporary stress of immunity against the background of vaccination. Literature data on identified adverse reactions when using inactivated vaccines to prevent a new coronavirus infection indicate a good profile safety," the manual says.
"It is not excluded the addition of acute (for example, acute respiratory viral infections, etc.) or exacerbation of chronic infectious diseases due to temporary stress of immunity against the background of vaccination. Literature data on identified adverse reactions when using inactivated vaccines to prevent a new coronavirus infection indicate a good profile safety," the manual says.
About the center and the vaccine
The Federal Research Center was established on the basis of the Institute of Poliomyelitis and Viral Encephalitis of the USSR Academy of Medical Sciences. The founder and first director of the Institute (until 1972) was Academician of the USSR Academy of Medical Sciences Mikhail Chumakov. The Center is one of the world's leading scientific institutions in the field of medical virology, including the study of enterovirus infections, tick-borne encephalitis, coronavirus and viral hepatitis. It has its own biotechnological production of vaccines for the vaccination schedule.