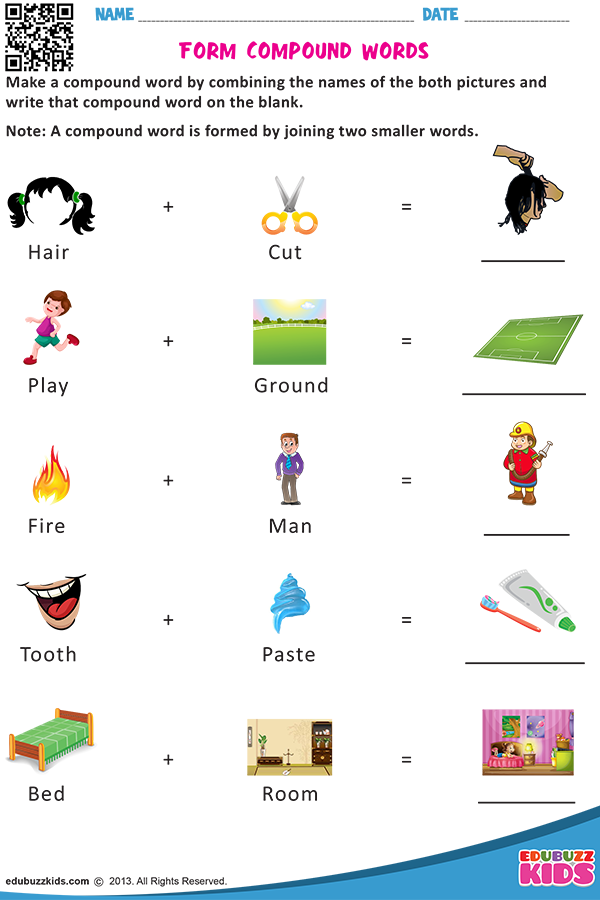
Print awareness examples
Print Awareness: An Introduction | Reading Rockets
Children with print awareness can begin to understand that written language is related to oral language. They see that, like spoken language, printed language carries messages and is a source of both enjoyment and information. Children who lack print awareness are unlikely to become successful readers. Indeed, children's performance on print awareness tasks is a very reliable predictor of their future reading achievement.
Most children become aware of print long before they enter school. They see print all around them, on signs and billboards, in alphabet books and storybooks, and in labels, magazines, and newspapers. Seeing print and observing adults' reactions to print helps children recognize its various forms.
The ability to understand how print works does not emerge magically and unaided. This understanding comes about through the active intervention of adults and other children who point out letters, words, and other features of the print that surrounds children. It is when children are read to regularly, when they play with letters and engage in word games, and later, when they receive formal reading instruction, that they begin to understand how the system of print functions; that is, print on a page is read from left to right and from top to bottom; that sentences start with capital letters and end with periods, and much, much more.
As they participate in interactive reading with adults, children also learn about books author's and illustrators names, titles, tables of content, page numbers, and so forth. They also learn about book handling how to turn pages, how to find the top and bottom on a page, how to identify the front and back cover of a book, and so forth. As part of this learning, they begin to develop the very important concept "word" that meaning is conveyed through words; that printed words are separated by spaces; and that some words in print look longer (because they have more letters) than other words.
Books with predictable and patterned text can play a significant role in helping children develop and expand print awareness. Typically these books are not decodable that is, they are not based on the sound-letter relationships, spelling patterns, and irregular/high frequency words that have been taught, as in decodable texts. Rather, predictable and patterned books, as the names implies, are composed of repetitive or predictable text, for example:
Typically these books are not decodable that is, they are not based on the sound-letter relationships, spelling patterns, and irregular/high frequency words that have been taught, as in decodable texts. Rather, predictable and patterned books, as the names implies, are composed of repetitive or predictable text, for example:
Two cats play on the grass.
Two cats play together in the sunlight.
Two cats play with a ball.
Two cats play with a toy train.
Two cats too tired to play.
Most often, the illustrations in such books are tied closely to the text, in that the illustrations represent the content words that change from page to page.
As they hear and participate in the reading of the simple stories found in predictable and patterned books, children become familiar with how print looks on a page. They develop book awareness and book-handling skills, and begin to become aware of print features such as capital letters, punctuation marks, word boundaries, and differences in word lengths.
Awareness of print concepts provides the backdrop against which reading and writing are best learned.
Print Awareness: Guidelines for Instruction
By: Texas Education Agency
Print awareness is a child's earliest understanding that written language carries meaning. The foundation of all other literacy learning builds upon this knowledge. The following are guidelines for teachers in how to promote print awareness and a sample activity for assessing print awareness in young children.
Guidelines for promoting print awareness
- The organization of books
Make sure students know how books are organized. They should be taught the basics about books – that they are read from left to right and top to bottom, that print may be accompanied by pictures or graphics, that the pages are numbered, and that the purpose of reading is to gain meaning from the text and understand ideas that words convey.
- Read to students
Read to children from books with easy-to-read large print.
 Use stories that have predictable words in the text.
Use stories that have predictable words in the text. - Use "big books" and draw attention to words and letters
Help children notice and learn to recognize words that occur frequently, such as a, the, is, was, and you. Draw attention to letters and punctuation marks within the story.
- Label objects and centers in your classroom
Use an index card to label objects and centers within the classroom with words and pictures. Use an index card with the word "house" for the house center and draw a picture of a house. Draw students' attention to these words when showing them the different centers.
- Encourage preschool children to play with print
They can pretend to write a shopping list, construct a stop sign, write a letter, make a birthday card, etc.
- Help children understand the relationship between spoken and written language
Encourage students to find on a page letters that are in their names: "Look at this word, 'big.
 ' It begins with the same letter as the name of someone in this room, 'Ben.'"
' It begins with the same letter as the name of someone in this room, 'Ben.'" - Play with letters of the alphabet
Read the book Chicka Chicka Boom Boom. Place several copies of each letter of the alphabet in a bowl and ask students to withdraw one letter. When everyone has a letter, ask each student to say the letter's name and, if the letter is in his or her own name, have the child keep the letter. Continue until the first child to spell his or her name wins.
- Reinforce the forms and functions of print
Point them out in classroom signs, labels, posters, calendars, and so forth.
- Teach and reinforce print conventions
Discuss print directionality (print is written and read from left to right), word boundaries, capital letters, and end punctuation.
- Teach and reinforce book awareness and book handling
- Promote word awareness by helping children identify word boundaries and compare words
- Allow children to practice what they are learning
Ask them to listen to and participate in the reading of predictable and patterned stories and books.

- Provide practice with predictable and patterned books
Also try using a wordless picture book like Pancakes. Go through each page asking the children to tell the story from the pictures. Write their narration on a large piece of paper. Celebrate the story they authored by eating pancakes!
- Provide many opportunities for children to hear good books and to participate in read-aloud activities
A sample activity for assessing print awareness
Give a student a storybook and ask him or her to show you:
- The front of the book
- The title of the book
- Where you should begin reading
- A letter
- A word
- The first word of a sentence
- The last word of a sentence
- The first and last word on a page
- Punctuation marks
- A capital letter
- A lowercase letter
- The back of the book
Excerpted and adapted from: Guidelines for Examining Phonics and Word Recognition Programs, Texas Reading Initiative, Texas Education Agency (2002). And from: Tips for Teaching Kids to Read; by Ed Kame'enui, Marilyn Adams, & G. Reid Lyon.
And from: Tips for Teaching Kids to Read; by Ed Kame'enui, Marilyn Adams, & G. Reid Lyon.
Related Topics
Curriculum and Instruction
Early Literacy Development
Print Awareness
New and Popular
100 Children’s Authors and Illustrators Everyone Should Know
A New Model for Teaching High-Frequency Words
7 Great Ways to Encourage Your Child's Writing
All Kinds of Readers: A Guide to Creating Inclusive Literacy Celebrations for Kids with Learning and Attention Issues
Screening, Diagnosing, and Progress Monitoring for Fluency: The Details
Phonemic Activities for the Preschool or Elementary Classroom
Our Literacy Blogs
Shared Reading in the Structured Literacy Era
Kids and educational media
Meet Ali Kamanda and Jorge Redmond, authors of Black Boy, Black Boy: Celebrating the Power of You
Get Widget |
Subscribe
Real examples of IS awareness raising and cyber exercises for management
I will start with short reviews of the past in Moscow "IS Code. Pro", where I happened to be the curator of the program, which was devoted to various aspects of information security management. One of them is to raise awareness and train employees of different levels - from ordinary workers to top management. This topic was originally devoted to 3 reports, but one at the last moment did not happen for a good reason. Therefore, I will only talk about two of them.
Pro", where I happened to be the curator of the program, which was devoted to various aspects of information security management. One of them is to raise awareness and train employees of different levels - from ordinary workers to top management. This topic was originally devoted to 3 reports, but one at the last moment did not happen for a good reason. Therefore, I will only talk about two of them.
The first one was made by Kirill Martynenko from Sberbank, who talked about the evolution of technologies for raising awareness, training employees and building an information security culture in them. Given the practical focus of the master class and the scale of Sberbank, Kirill's story turned out to be very informative. Especially given the manner in which the material was presented, which described typical approaches to "culturing" with its pluses and minuses.
Like many organizations, Sberbank also started with various tests, a kind of anachronism in the field of training, which is still actively implemented by many companies due to its simplicity, but complete uselessness for people who are not involved in the daily process of ensuring information security. For non-specialists, all these tests are a waste of time, since after they are completed there is little to remember, and even more so they do not provide any skills that should be the goal of any program for building a culture of information security.
For non-specialists, all these tests are a waste of time, since after they are completed there is little to remember, and even more so they do not provide any skills that should be the goal of any program for building a culture of information security.
Just like a toast, which should be as short as a shot, the information conveyed to employees should be short, clear and understandable. And since it is necessary to infiltrate the brain of employees wherever possible (and not only through screensavers on a computer), posters that are hung in completely different places are great for this purpose - in the canteen, near the printing places, near the elevators, etc. P.
Kirill Martynenko showed several examples of such posters and talked about the peculiarities of their development and placement at Sberbank.
In addition to passive information, it is also necessary to regularly check the skills of employees to counter the ever-evolving methods of intruders. Kirill spoke about several campaigns that were launched across Sberbank to test how well posters, tests, screensavers and other ways of communicating information security rules to all employees of the largest bank in the country work. For example, an interesting snag in the form of the supposedly created airline "Sberbank Airlines", which offered tickets to different parts of the world "at a discount". Considering Sber's various fields of activity, such promotional messages sent by e-mail looked quite plausible.
Kirill spoke about several campaigns that were launched across Sberbank to test how well posters, tests, screensavers and other ways of communicating information security rules to all employees of the largest bank in the country work. For example, an interesting snag in the form of the supposedly created airline "Sberbank Airlines", which offered tickets to different parts of the world "at a discount". Considering Sber's various fields of activity, such promotional messages sent by e-mail looked quite plausible.
The Black Friday phishing campaign exploited the desire of people to get something at a discount and participate in charity.
But the technology of immersion in the human brain does not stand still, and therefore Sberbank began to develop and implement various games, simulations, screensavers and videos created using Flash technology. One of such developments was the interactive game "Cybersecurity Agent", which in a playful way allows employees not only to get acquainted with the necessary information security rules, but also to check them in the virtual world, increasing memorability and engagement.
The apotheosis of the master class, conducted by Kirill Martynenko, was the story and demonstration of the use of virtual reality in raising awareness of information security.
Kirill demonstrated two VR projects that have already been implemented in the "green bank". The first one is a regular shooter, where various IS threats are chosen as targets, which must be destroyed with the help of virtual weapons.
The second project is a virtual visit to the Sberbank Cyber Defense Center (SOC). At last year's RSA exhibition in San Francisco, a lot of projects for the use of VR in information security were presented (they are also used in Cisco), and now they are available in Russia. Yes, it is clear that not everyone can afford to introduce such innovations to form an information security culture, but the demonstration of such projects itself was very, very interesting.
In my master class, I already continued the topic of gamification in information security, but from a slightly different angle - I talked about how to conduct cyber security exercises for the top management of an enterprise. It so happened that I still can't forget how Rustem Khairetdinov said a year ago that I'm a shitty speaker. His criticism sunk into my soul and I began to immerse myself in new methods of conveying information to people, moving away from a lecture monologue towards dialogue, involving participants in a discussion, gamification, etc. And then they began to invite them to speak to high-ranking officials of various companies, to whom it makes no sense to give presentations that are so familiar to ordinary IS specialists.
It so happened that I still can't forget how Rustem Khairetdinov said a year ago that I'm a shitty speaker. His criticism sunk into my soul and I began to immerse myself in new methods of conveying information to people, moving away from a lecture monologue towards dialogue, involving participants in a discussion, gamification, etc. And then they began to invite them to speak to high-ranking officials of various companies, to whom it makes no sense to give presentations that are so familiar to ordinary IS specialists.
This is how the topic of conducting cyber exercises for top management was born, which, of course, require a completely different preparation, but the effect of them will be fundamentally different from the passive and one-sided presentations that people listen to, but often remember what was said there. Following the rule that only 10% of what is read is assimilated, only 20% of what is heard, 30% of what is seen, 90% of what is worked out in the exercises, it is involvement that allows you to convey the necessary information to such a difficult audience, such as leaders of various stripes - CEO , CFO, CLO, COO, etc.
It's hard to retell myself, so I'll post a few slides from the master class that I read at "IB Code. Profi". True, I did not get the original material for the hour that was allocated at the conference, but for 3-4 hours (or even more). But I had to shrink :-)
The third report on gamification in information security was supposed to be done by Vyacheslav Borilin from Kaspersky Lab, but for a good reason he could not be at the event. Vyacheslav should provide a base on the topic of gamification and our master classes with Kirill and show with various examples what works best in different learning formats - full-time, online, mixed format; including for different audiences - ordinary employees, managers, top management. Alas, it didn't work out. But Vyacheslav promised to record a separate webinar for the participants "IB Code. Profi" - it will be posted, like all materials, on the conference website.
PS. Participants of Code IB. Profi can get access to presentations and videos of all master classes as part of their purchased package. For those who could not participate in person, but would like to get acquainted with all the materials, there is an opportunity to purchase the "CONTENT" package, which will not replace personal presence and the opportunity to ask questions, but still allow you to immerse yourself in the practice of information security management from one of the best speakers Russia in Information Security, who are also mainly practitioners in the field of cybersecurity.
Profi can get access to presentations and videos of all master classes as part of their purchased package. For those who could not participate in person, but would like to get acquainted with all the materials, there is an opportunity to purchase the "CONTENT" package, which will not replace personal presence and the opportunity to ask questions, but still allow you to immerse yourself in the practice of information security management from one of the best speakers Russia in Information Security, who are also mainly practitioners in the field of cybersecurity.
The world is going crazy and the cyber apocalypse will break out. Subscribe to our Telegram channel to be the first to know how to survive in the digital nightmare!
Increasing employee awareness: your contribution to security
Increasing employee awareness of cybersecurity rules is one of the eternal trends in the information security industry. And one of those that is especially often neglected, according to annually published statistics. Financial losses, operational failures, the loss of partners and customers and, as a result, the deterioration of the business image occur much more often than one might think.
Financial losses, operational failures, the loss of partners and customers and, as a result, the deterioration of the business image occur much more often than one might think.
- Introduction
- Full-time vs remote
- Getting Started
- Distance learning trends
- Testing knowledge
- Do not forget about reality
- Help print
- Pins
Introduction
Any self-respecting company has internal regulations, policies and practices dedicated to the rules for storing and processing confidential information. Alas, the mere presence of these documents does not give absolutely nothing. Real protection is provided by employees who strictly follow the requirements prescribed in the documents. But where to find such ideal defenders?
The trick is not to look for them, but, let's say, to grow them. A set of activities and materials aimed at raising awareness in the field of information security helps to create a culture of working with valuable data in the company. If everything is chosen correctly, employees begin to follow the rules of information security on a reflex level - and you no longer have to worry that one of them does not block the computer screen, lose a token, or forget the quarterly report in the printer tray.
If everything is chosen correctly, employees begin to follow the rules of information security on a reflex level - and you no longer have to worry that one of them does not block the computer screen, lose a token, or forget the quarterly report in the printer tray.
Face-to-face vs remote
It's no secret that most Russian companies train their employees, if at all, in the old fashioned way, in person. Most often, these are introductory information security briefings for beginners, which are conducted by employees of the relevant departments. More rarely, briefings are supplemented by mailing lists with excerpts from the already mentioned regulations and confidential information policies.
The same statistics show that this approach no longer works. All over the world, face-to-face learning is rapidly giving way to distance learning. And there are a number of reasons for this. The most pleasant thing for business is cost reduction: electronic materials are developed and bought once, and used as long as necessary.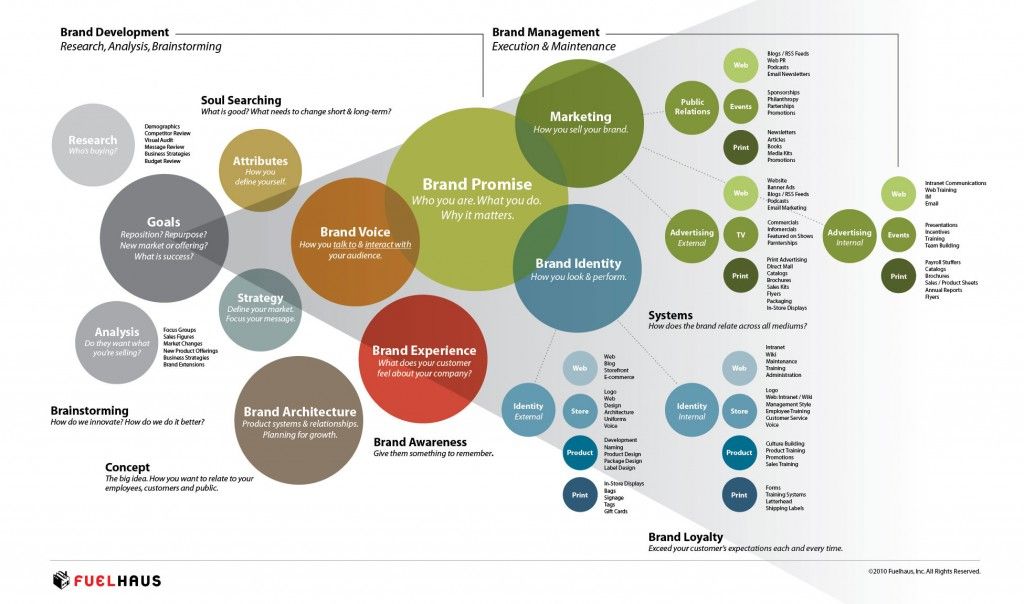 Another reason to choose e-learning is convenience: interactive courses, videos and browser games can be viewed on different types of devices - computer, tablet or smartphone - at any time. It is also important that when choosing distance learning, events are held for an unlimited number of employees, in different regions of the country - without the cost of visiting trainers and solving organizational issues.
Another reason to choose e-learning is convenience: interactive courses, videos and browser games can be viewed on different types of devices - computer, tablet or smartphone - at any time. It is also important that when choosing distance learning, events are held for an unlimited number of employees, in different regions of the country - without the cost of visiting trainers and solving organizational issues.
There is an advantage that is not obvious at first glance: everyone has long known what to expect from full-time education. Roughly speaking, it is not able to surprise the employee, to really involve him in the process of raising awareness. At the same time, distance learning demonstrates new methods and technologies every year. Online simulators, business process simulators, VR cases, multiplayer games - all these formats prove that e-learning will not reach its "ceiling" for a very long time.
Figure 1. Examples of distance learning materials.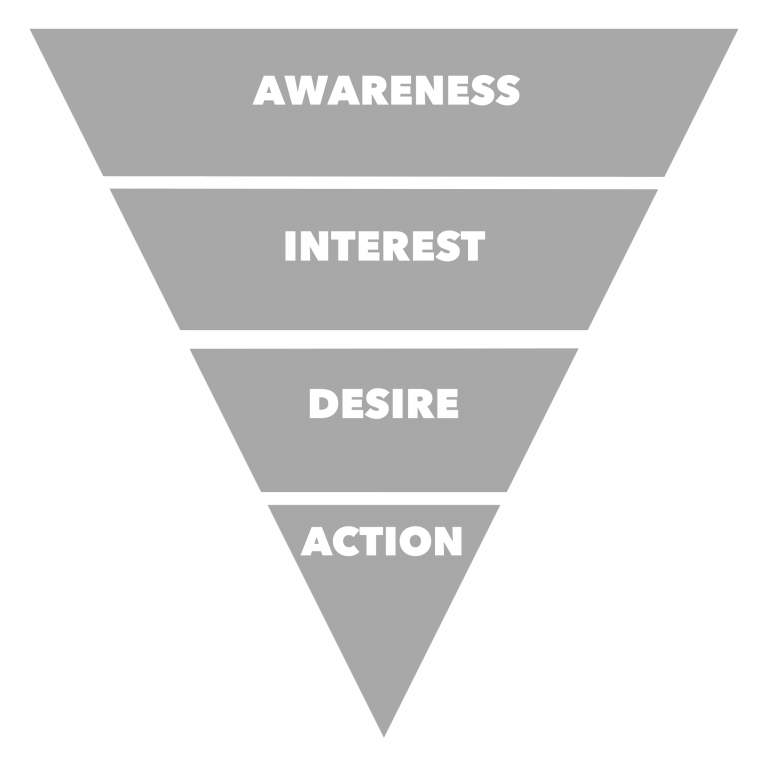 Electronic courses
Electronic courses
Where to start
Of course, with the target audience. Divide your employees into groups and find topics relevant to each of them. Top managers are unlikely to be interested in studying software vulnerabilities, and for developers, this is one of the main aspects of information security.
Once the topics are defined, think about the formats of the teaching materials: these too need to be personalized. For example, front office employees do not have much free time, and sometimes they do not have a personal working computer. Short videos and bright posters are suitable for them - they can be placed and displayed both in work areas and in rest rooms. Back-office employees can pay more attention to training, so it is better for them to address e-courses with included knowledge testing and periodic mailing lists.
Another good practice is to check what your employees already know before conducting information security training. The easiest way to do this is to test, even a small one, and send emails that mimic real malware. By collecting statistics, you will understand which topics you need to focus on.
The easiest way to do this is to test, even a small one, and send emails that mimic real malware. By collecting statistics, you will understand which topics you need to focus on.
Distance learning trends
Actually, I have already mentioned one of the trends - personalization, development of materials taking into account the needs of the target audience. Personalization can be achieved not only through the selection of different formats, but also with the help of variability within one of them - for example, by creating several trajectories for passing an electronic course, making it possible to choose the complexity of practical tasks or repeat the material covered. If an employee understands that he is given a certain degree of freedom, the learning process becomes more enjoyable and less stressful for him, which means it brings better results.
The next e-learning trend is gamification. In addition to the games themselves, gamification is also actively used in e-learning courses. It involves adding game elements to the materials - characters, animation, a fascinating and non-standard plot. Tasks in gamified courses, as a rule, gradually become more difficult, and rewards are given to employees for their successful completion. The main thing here is not to play too much, to combine business with pleasure in exactly the proportion that will give the maximum learning effect.
It involves adding game elements to the materials - characters, animation, a fascinating and non-standard plot. Tasks in gamified courses, as a rule, gradually become more difficult, and rewards are given to employees for their successful completion. The main thing here is not to play too much, to combine business with pleasure in exactly the proportion that will give the maximum learning effect.
Finally, another trend is microlearning. It involves the presentation of theory in small blocks and the consolidation of each of them in practice. For example, after five or six course slides, the user must answer a test question or complete a simple exercise. If we are talking about videos, then it is better to make them no more than two minutes long. Three short videos, united by a funny plot, will be much more useful for employees than a painful six-minute sermon. However, it is not worth splitting the training to infinity: it is so easy to lose both the logic of the narrative and the interest of the audience.
Figure 2. Examples of distance learning materials. Browser games
Checking knowledge
Tests, exercises and case studies in electronic courses, as well as simulators and business simulators aimed at working out a clear sequence of actions, most often act as a means of testing knowledge. In any case, they are mainly effective when you can track how well the company's employees pass them. And this means that it is highly desirable for you to acquire a distance learning system (LMS) and upload materials already into it. The market offers enough options - it will not be difficult to choose the right one.
Earlier I mentioned mailing lists imitating malicious emails. It is also good to use training phishing mailing lists for periodic knowledge testing. In this case, they are sent to users selectively, according to different scenarios and in different templates - and go in close conjunction with the main training materials. For example, if your employee “succumbed to provocation” and opened a compiled phishing email, then he can be re-sent to study a course on social engineering. By the way, some LMS include a training phishing module - also a reason to think about acquiring such a system.
For example, if your employee “succumbed to provocation” and opened a compiled phishing email, then he can be re-sent to study a course on social engineering. By the way, some LMS include a training phishing module - also a reason to think about acquiring such a system.
Do not forget about reality
Learning becomes doubly enjoyable when its results can be compared with the achievements of other users, and even better - seen in real life. With the first, the creation of training ratings and the selection of leaders will help. In a number of LMS there is such an opportunity, and if not, the rating can simply be placed and updated on the corporate portal. Visualization can be very different, from the standard conquest of mountain peaks to, say, the passage of the evolutionary process.
As for real life, here we need to remember about gamification and its characteristic systems of achievements - medals, cups, stars, shields (there is no escape from associating information security with a shield).